Title Page
-
Conducted on
-
Site Name / Location
-
Prepared by
-
Personnel supporting audit
-
Document No.
-
THE INFORMATION CONTAINED IN THIS DOCUMENT IS CONFIDENTIAL AND IS NOT TO BE COMMUNICATED TO ANY PERSON OTHER THAN AUTHORISED EMPLOYEES.
Executive Summary
-
A physical site security risk assessment was conducted using a Comparative Risk Assessments process. The Risk Assessment looks at the facility attractiveness, known threats, and vulnerabilities to enable recommendations to be implemented to mitigate risk. The Security Vulnerability Assessment highlighted areas of risk which are likely to affect the overall security of the site, based on these findings the current vulnerability of this site to known threats is classified as: -
- Low - Resistant and robust to identified threat(s) but requires awareness
- Medium - Resistant to threats but with some weakness
- High - Limited resistance to the threats
- Very High - Little or no resistance to the threats
-
Consideration should be made to the vulnerability findings listed in this report to help improve the overall security of the site to known threats.
This Security Vulnerability Assessment [SVA] forms a vital part of identifying any potential vulnerabilities in physical security measures, security systems, policies, processes, procedures, and personnel, that may cause risk to the business.
The information gained to compile this security vulnerability assessment was gathered through conducting an in-depth site inspection of current existing and/or natural mitigation security measures. -
RISK TOLERANCE - Currently the risk tolerance is purely for example only. Tolerances to be decided when risk appetite is agreed.
-
Very High - Business feels most concerned about this risk. Disastrous impact on business activities and clients. Comprehensive and immediate action is required.
-
High - Business feels concerned about carrying this risk. The consequences of the risk materialising would be severe but not disastrous. Some immediate action is required plus the development of a comprehensive action plan.
-
Medium - Business is uneasy about this risk. Consequences of the risk on the business are not severe and can be managed via contingency plans. Action plans developed later, and budget bids mobilised. Status of risk should be monitored regularly.
-
Low - Business is content to accept this risk. Consequences of risk relatively unimportant to the business. Status of risk should be reviewed periodically
Key Assets / Locations
Key Assets
-
Staff, Visitors, Contractors & other individuals present on the site.
-
Intellectual property inclusive of high value, sensitive information and data concerning clients business interests either on computer, servers or files.
-
Intangibles; clients image, reputation, financial strength and future profitability
-
Site property inclusive of the buildings, technical and IT equipment
-
Controlled Drugs
-
Products
-
Manufacturing Equipment / Plant
Key Locations
-
Select Key Asset Locations
- Warehouse
- Office
- Production
- Data Centre
- High Value Store
- Controlled Drug Store
- Animal Unit
- Goods In / Out
- Waste Destruction
- Energy Unit
-
Rationale
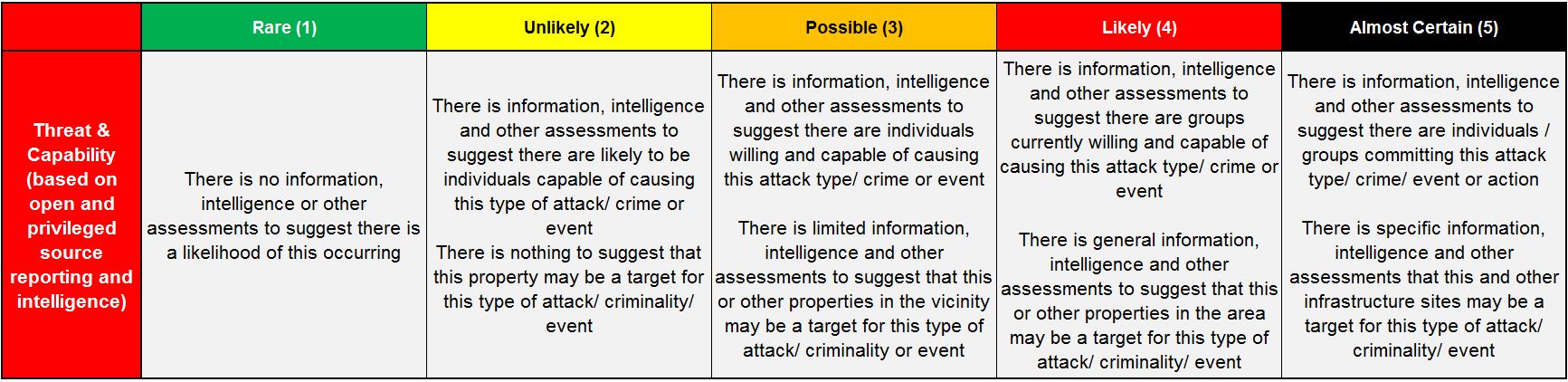
Threat Assessment
-
Assessment of the threat against the following categories will be based on and supported by credible intelligence sources or events that have taken place in the past 5 years.
-
Theft - Internal
-
Rationale
-
Theft - External
-
Rationale
-
Public Order Protest
-
Rationale
-
Site Penetration
-
Rationale
-
Major Disaster
-
Rationale
-
Direct Protest Activity
-
Rationale
-
Workplace Violence
-
Rationale
-
Low Level Crime
-
Rationale
-
Violation of Policy
-
Rationale
-
Terrorism
-
Rationale
-
Inside Threats
-
Rationale
Vulnerability Findings / Recommendations
-
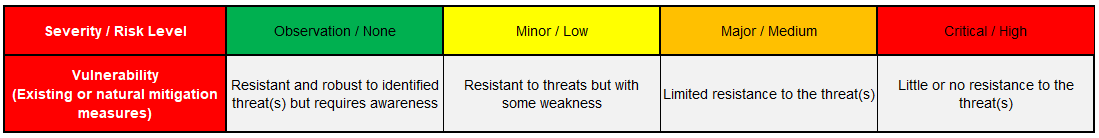
Vulnerabilities are then assessed against resistant to perceived threats that have been highlighted and given a severity / risk level rating according to the following vulnerability criteria to enable informed decision on highlighted findings / recommendations to be made.
- Finding #
-
Location
-
Severity / Risk Level
- Observation / None - Resistant and robust to identified threat(s) but requires awareness
- Minor / Low - Resistant to threats but with some weakness
- Major / Medium High - Limited resistance to the threat(s)
- Critical / High- Little or no resistance to the threat(s)
Summary / Comments
Disclaimer
-
All information contained in this document is confidential and is not to be used for any other purpose or disclosed wholly or in part to any other party without prior permission in writing being granted by the author.
This restriction does not cover information published or information that can be demonstrated was publicly available on the date of this document.
Copyright and intellectual property rights in all documents and drawings supplied by the author are vested in the author of the report. The recipient accepts this proposal on the basis that this document may not be copied unless agreed in writing by the author.
We reserves the right at any time to request that all copies of this document be returned. The recipient agrees to return all copies of this document forthwith upon receipt of such request.
All details were correct at the time of writing the report however some of these items may be have been rectified.