Title Page
SHIP SECURITY ASSESSMENT ON BOARD
-
NAME OF YACHT
-
Conducted on
-
Prepared by
-
Location
FOLLOW UP ASSESSMENT IN OFFICE
-
IYC OFFICE:
-
Select date
ARRIVAL AT THE VESSEL
First Impressions
-
Is there a "No Visitor" sign posted on the passerelle/gangway?
-
Is there a sign stating: "All contractors and approved guests must report to a crew member before boarding."
-
Is the Passerelle in a safe operating condition?
-
Is there a visitors log book available and in use near the boarding area?
-
Is there a sign at the boarding area stating the MARSEC Level?
INFORMATION & DOCUMENTATION
OWNING COMPANY INFORMATION
-
Name of Owning Company
-
Address of Owning Company
-
IMO Number of Owning Company
VESSEL INFORMATION
-
Year of Build
-
IMO number
-
The IMO number is permanently fixed where? (e.g. "in the Engine Room & ship's brow"
-
Official Number
-
Flag State
-
Home Port
-
Call Sign
-
Class Society
-
Type of Vessel
-
Is this a commercial (charter) yacht or a private yacht with voluntary compliance?
-
LOA
-
Draft
-
Gross Tonnage
-
Net Tonnage
-
Number of Crew Members
-
Nationalities of Crew Members
-
Working Language On Board
-
Cruising areas this vessel will visit:
CONTINUOUS SYNAPSIS RECORD (CSR)
-
A Continuous Synapsis Record has been issued by the Flag State Administration in the format required by the Regulation.
-
A request for issuing a new CSR with the updated owner and management company info has been forwarded to the Flag State.
COMMUNICATION EQUIPMENT ON BOARD
-
List different types of comm. equipment here
CONSIDERATIONS FOR THE ASSESSMENT
THE FOLLOWING WERE TAKEN INTO CONSIDERATION WHEN FORMULATING THIS SSA:
-
- The future navigational area of the vessel - Identification of possible threats and security risks - Identification and evaluation of keyboard shipboard operations - Possible threat scenarios and the likelihood of occurrence - Existing security measures and procedures in effect - Identification of weakness, including human factors
ALL POSSIBLE THREATS WERE CONSIDERED, INCLUDING:
-
- Damage to, or destruction of, the vessel, e.g. by explosive devices, arson, sabotage or vandalism - Hijacking or seizure of the ship or of persons on board - Tampering with essential ship equipment or systems or ship’s stores - Unauthorized access or use, including presence of stowaways - Smuggling weapons or equipment - Use of the ship to carry those intending to cause a security incident and/or their equipment - Use of the ship itself as a weapon or as a means to cause damage or destruction - Attacks from seaward whilst at berth or at anchor - Attacks whilst at sea.
ALL POSSIBLE VULNERABILITIES WERE TAKEN INTO ACCOUNT INCLUDING:
-
- Conflicts between safety and security measures - Conflicts between shipboard duties and security assignments - Watch-keeping duties, number of ship’s personnel (particularly with implications on crew fatigue, alertness and performance) - Identified security training deficiencies - Security equipment and systems, including communications systems.
THREAT ASSESSMENT
THREAT ASSESSMENT
-
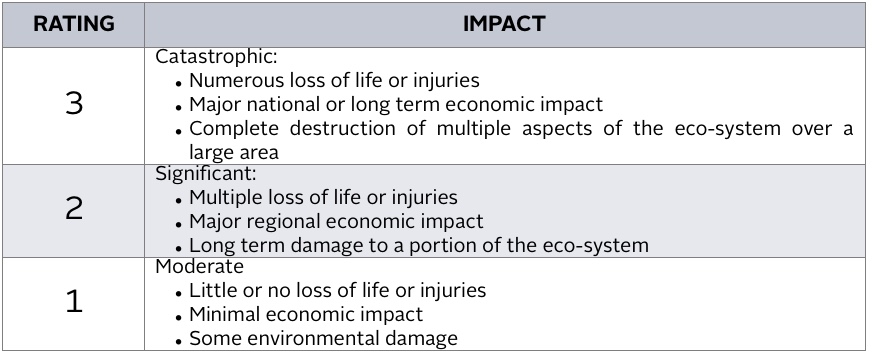
CONSEQUENCE SCORE
-
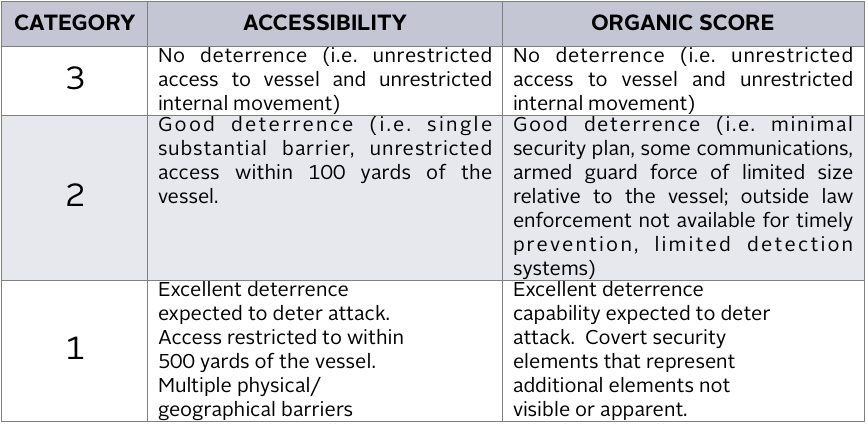
VULNERABILITY SCORE
-
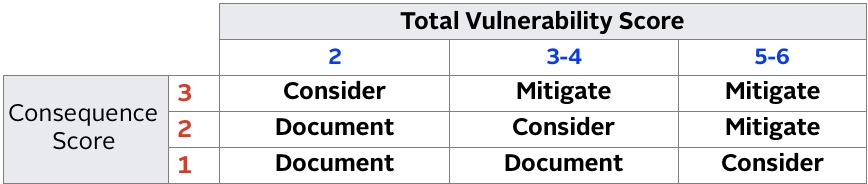
VULNERABILITY & CONSEQUENCE MATRIX
-
MITIGATE means that mitigation strategies, such as security protective measures and / or procedures, may be developed to reduce risk for that scenario.
CONSIDER means that the scenario should be considered and mitigation strategies should be developed on a case-by-case basis.
DOCUMENT means that the scenario may not need a mitigation measures at this time and therefore needs only to be documented. -
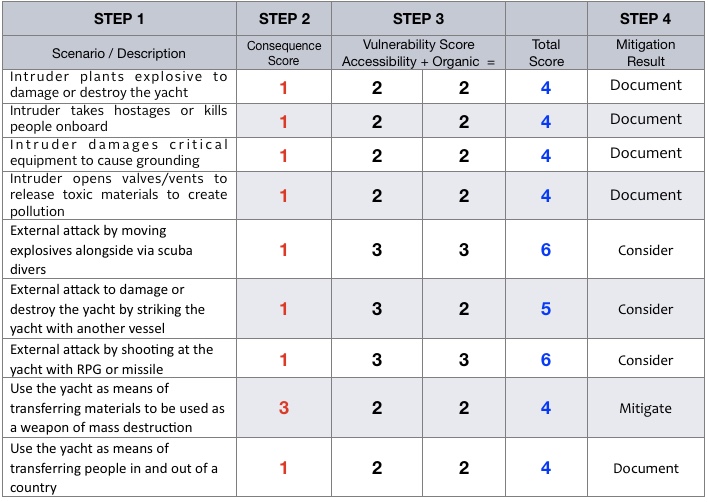
MITIGATION DETERMINATION WORKSHEET
THREATS
Vessel information relevant to the following threats described:
-
Vessel LOA
-
Maximum persons on board (crew and guest)
-
Maximum fuel capacity
INTRUDER PLANTS EXPLOSIVES TO DAMAGE OR DESTROY THE YACHT
-
The worst possible outcome would be destruction and sinking of the yacht. The greatest possible loss of life would be the max persons listed above (assuming no other vessels are involved). The economic impact would be limited to the value of the yacht, it’s contents, possibly nearby structure, salvage costs and loss of use of the dock if alongside. It is unlikely that a sunken yacht of this length could block or otherwise interrupt major trading routes to cause significant economic impact. Maximum impact to the environment would be spillage of max capacity of fuel. There is little deterrence from boarding the yacht at night; however, access to the interior spaces is well restricted. Surveillance cameras cover the exterior access points and monitored as described elsewhere in this document while all entrances to the interior of the yacht can be locked. Entrance doors are equipped with intruder alarm as described elsewhere in this document. The yacht itself is an unlikely target. The yacht’s owner and guests may raise the yacht’s likelihood of becoming a target.
INTRUDER TAKES HOSTAGES OR KILLS PEOPLE ON BOARD
-
The greatest possible loss of life would be the max persons listed above. The economic impact would be limited to a ransom amount and possible minor damage to the yacht. No environmental damage would occur. There is little deterrence from boarding the yacht at night; however, access to the interior spaces is well restricted. Surveillance cameras cover the exterior access points while all entrances to the interior of the yacht can be locked and entrance doors monitored from three different locations onboard. The yacht is unlikely to sail in high risk areas such as the coast of Somalia and Malacca Straits. If sailing in such area, additional security measures may be required. The perceived wealth of those associated with the yacht increases the risk of becoming a target for hostage taking.
INTRUDER DAMAGES CRITICAL EQUIPMENT TO CAUSE GROUNDINGS
-
The worst possible outcome would be destruction and sinking of the yacht. The greatest possible loss of life would be the max persons listed above – although it is likely that all persons could be evacuated to survival crafts. The economic impact would be limited to the value of the yacht, its contents, and salvage costs. It is unlikely that a sunken yacht of this length could block or otherwise interrupt major trading routes to cause significant economic impact. Maximum impact to the environment would be spillage of max capacity of fuel and possible localized coral reef damage. There is little deterrence from boarding the yacht at night; however, access to the interior spaces is well restricted. Surveillance cameras cover the exterior access points and monitored as described elsewhere in this document while all entrances to the interior of the yacht can be locked. Entrance doors are equipped with intruder alarm as described elsewhere in this document. The yacht is less likely target relative to a tanker, cargo or passenger vessel.
INTRUDER OPENS VALVES/VENTS TO RELEASE TOXIC MATERIALS TO CREATE POLLUTION
-
Loss of human life or damage to humans is highly unlikely. The economic impact would be limited to the value of the materials lost and possible minor damage to the yacht. Maximum impact on the environment would be the max capacity of fuel.
EXTERNAL ATTACK BY MOVING EXPLOSIVES ALONGSIDE VIA SCUBA DIVERS
-
The worst possible outcome would be destruction and sinking of the yacht. The greatest possible loss of life would be the max persons listed above (assuming no other vessels are involved). The economic impact would be limited to the value of the yacht, its contents, and salvage costs and possibly nearby structure. It is unlikely that a sunken yacht of this length could block or otherwise interrupt major trading routes to cause significant economic impact. Maximum impact on the environment would be spillage of the max capacity of fuel. There is little deterrence to accessing the yacht from underwater. Security patrols on deck would be very limited in their ability to detect attackers (especially if re-breathers are used). For an underwater charge to be most effective, particulars of the yacht’s structure would be required. The level of expertise required of the attacker would be high (i.e. underwater navigation skills, access to the appropriate explosives and detonation devices, means to transport the materials underwater) and would require a very dedicated attacker. The yacht itself is an unlikely target. Some of the yacht’s crew should be proficient SCUBA divers. In the event additional measure is required, the crew could make underwater inspections of the hull and adjacent structure.
EXTERNAL ATTACK TO DAMAGE OR DESTROY THE YACHT BY STRIKING THE YACHT WITH ANOTHER VESSEL
-
This scenario will not address damage to or loss of life upon the other vessel involved. The worst possible outcome would be destruction and sinking of the yacht. The greatest possible loss of life would be the max persons listed above. The economic impact would be limited to the value of the yacht, its contents, and salvage costs and possibly nearby structure. It is unlikely that a sunken yacht of this length could block or otherwise interrupt major trading routes to cause significant economic impact. Maximum impact on the environment would be spillage of the max capacity of fuel. While the yacht may implement evasive maneuvers if at sea, there is little to stop the attack if the other vessel is faster or more maneuverable. While the yacht is at the dock, waterborne patrols can do little to stop another vessel from striking the yacht. The yacht itself is an unlikely target.
EXTERNAL ATTACK BY SHOOTING AT THE YACHT WITH A ROCKET PROPELLED GRENADE OR MISSILE
-
This scenario assumes the missile is transportable by humans (as opposed to a vehicle launched device). A missile would likely result in the loss of 3 or 4 lives or less. The greatest possible loss of life would be the max persons listed above. The economic impact would be limited to the damage caused to the localized area of the yacht and its equipment. It is unlikely that the yacht would sink as a result of the attack. Fuel or lube oil would likely not be spilled. No other impact on the environment would be likely. The yacht’s crew is very limited in their ability to deter this action. Deploying a rocket propelled grenade or missile against the yacht would be relatively simple and require little expertise. The yacht itself is an unlikely target. The yacht’s presence at a high profile event (i.e. the Olympics or a film festival) or the profile of guests may raise the yacht’s likelihood of becoming a target.
VULNERABILITIES
In accordance with ISPS Part B, section 8.10 the relevant vulnerabilities to the security of this vessel have been assessed below.
-
Access to the yacht while alongside may be difficult to control. Depending on the mooring arrangements and height of the pier, the swim platform may be easily accessible without the need for a gangway or ladder. The crew is typically on deck during normal working hours. They are busy with their deck / interior / engineering duties and some are additionally busy with ISM requirements. Attending the gangway and checking in visitors will increase the burden on the crew. Doors to the interior will be locked, but access to the exterior decks of the yacht will be difficult to monitor during late night hours. Countermeasures to address this vulnerability may include special mooring arrangements, motion detectors to an alarm, and / or additional crew for watch standing.
-
Surveillance cameras cover the exterior access points and monitored as described elsewhere in this document while all entrances to the interior of the yacht can be locked. Entrance doors are equipped with intruder alarm as described elsewhere in this document.
-
Ship's stores are located in various locations around the yacht. If any stores are accessible from the exterior of the vessel, describe the ability and/or procedure for securing these locations.
-
The Restricted Areas of the yacht should have a means of locking and securing access to them. This is described in the Restricted Areas section.
-
Other areas with sensitive contents are not identified as restricted areas. Examples include: spaces such as the accommodation areas, bow thruster, HVAC spaces, potable water tanks and systems, bunkering connections, antennas on the mast, ship’s stores. Due to the layout of the yacht, it would be impractical to make these areas restricted.
Existing crew hiring procedures include the captain reviewing the candidate’s resume, checking references provided by the candidate and an interview with the candidate. Background checks are not currently performed. Countermeasures to address this vulnerability would include conducting background checks. More extensive background checks may be conducted by the owner and the captain.
The vessel’s relatively high freeboard does not allow for easy access by unauthorized persons except along the stern
CONCLUSION
-
The greatest challenge for the security of this yacht will be access control when the yacht is along side. To a lesser extent, the yacht will be challenged with access control at sea
RESTRICTED AREAS
POLICY
-
The following have been designated by the ISPS code and national maritime security legislation as Restricted Areas, to which access is to be strictly controlled and limited to authorized persons.
-
1. Bridge
2. Radio Room
3. ECR and Engine Room
4. Steering Gear -
It is IYC’s policy that all Restricted Areas are locked or otherwise secured where possible, unless the Master, CSO, or in the case of the Engine Room the Chief Engineer, decides that for particular and specific operation reasons, it is necessary to have them open.
There is little deterrence from boarding the yacht at night; however, access to the interior spaces is well restricted. -
Restricted areas are to be marked "No Admittance", "Authorized Personnel Only", or similar.
BRIDGE & RADIO ROOM
-
The doors to the bridge wings should be locked at all times when unattended unless the Master decides for operational reasons it shall be open
-
Describe all access points to the bridge and radio room and the means of securing them.
ENGINE CONTROL ROOM & ENGINE ROOM
-
At Security Level 1 the main access is kept open at all times. At a higher level of security the accesses to the engine room shall be kept locked at all times unless the Chief Engineer decides for operational reasons they should be open. If necessary, the doors and can be unlocked from the inside.
-
Describe all access points to the ECR and Engine Room and the means of securing them.
STEERING GEAR
-
Describe all access points to the Steering Gear and the means of securing them.
VULNERABLE POINTS
-
Examples of these could be but are not limited to Accommodation Entries, Bow Thruster Room, Fire Fighting Stations, Emergency Generator Room, Emergency Batteries for Navigation Equipment, Emergency Escapes, Bunker Stations, Potable Water Fills.
-
Describe the location, accessibility, and the ability to secure these Vulnerable Points.
ACCESS POINTS TO THE VESSEL
POLICY
-
It is IYC’S policy that all entrances to the vessel are closed; unless the Master or CSO decides there are operational reasons to have them open. All open access to the vessel should be protected
GANGWAYS & PASSERELLE
-
When the vessel is moored, with guests onboard one watchman controls the gangway on elevated security level.
Gangway Watch responsibilities, while in port, are:
- Maintain integrity of the gangway
- Ensuring that all visitors are logged in and out
- Ensuring that visitors are escorted when necessary
- Maintaining vigilance on the alongside of the vessel
- Reporting any suspicious activities or incidents to the OOW or SSO
- Reporting the present of any visitors or authorities to the OOW or SSO
- Carrying out searches of personnel or effects when required
EMERGENCY ESCAPE HATCHES
-
Are the emergency escape hatches in the guest cabins and machinery spaces clearly marked?
-
Are the emergency escape hatches easily accessible and not blocked by furniture or other obstructions.
-
Are the emergency escape hatches not able to be opened from the vessels exterior?
Physical Security
-
Can the doors from the bridge to the wing station be locked?
-
Can access door to the bridge from the interior by locked?
-
Can you lock all doors leading from the accommodation to the decks or are they only equipped with intruder alarm?
-
Can the bunkering locations be locked?
-
Can you lock all entrances to the engine room or are they only equipped with an alarm?
-
Are the door keys/passcodes controlled in a custody log?
PROVISIONS/STORES
-
Stores and provision will be loaded by the crew. All stores and provisions will be stored immediately in designated area following delivery.
MOORING LINES
-
Mooring lines are used on the forward and aft mooring decks. These areas are a possibility to seek unauthorized access to the vessel. The Port Facility and Shoreside Security are generally responsible for the security of mooring lines if present.
ANCHOR CHAINS
-
It is impossible to seek access to the vessel by entering the anchor chain hawsepipe due to the narrow diameter.
CONTROL, MONITORING, & INSPECTION PROCEDURES
SCREENING PROCEDURES POLICY
-
All persons and items brought on board the this vessel are liable to be searched. Persons refusing to comply with Company policy should be denied access and will be reported to the appropriate authorities.
Controlling and limit of visitor’s access will be in according to company procedures in according to ship security plan (SSP).
All screening of baggage for guests and crew member will be outlined in the SSP. The yacht reportedly does not accept unaccompanied baggage. Owners and guests arrive with their personal baggage and the crew hand carries all luggages to the appropriate guest stateroom. The guest luggage is unpacked by the crew.
Properly identified Duly Authorized Officers of Contracting Governments and their belongings are not subject to search prior to boarding and can not be denied access to the vessel.
VISITORS IDENTIFICATION / VISITORS LOG
-
The number of visitors allowed onboard the vessel is limited, and strictly controlled.
Crew members wishing permission to have visitors onboard must inform the Master or Chief Officer of the visitors. The visitors must sign the visitor’s log.
After approval the Master or Chief Officer complete the visitor pass including name, port, date of issue and period of validity.
Shoreside Visitors: On arrival at the ship, the identification of the visitor is established, eg: by driver license, passport or other valid ID.
Visitor Identification log: A visitor Identification Log is maintained by the gangway watch. This log records the name of the visitor, the person to be visited and time in out.
KEYS
-
Are crew given individual keys as necessary to perform their duties?
-
Lost or stolen keys to any restricted area are to be immediately reported to the SSO who shall take appropriate action to secure unauthorized access to the area.
SECURITY EQUIPMENT/COMMUNICATIONS/FIREARMS
SSAS (SOLAS Ch. XI-2, Regulation 6)
-
A Ship Security Alert System in addition to LRIT is installed on board the vessel.
-
Enter locations of both SSAS buttons. Include photos if possible.
-
Procedures, instructions and guidance on the use of the Alert System, including the testing, activation, de-activation and re-setting are known to the SSO.
-
An SSAS test was conducted, verifying both e-mail and text confirmation.
LIGHTING
-
Describe any exterior location unable to be illuminated by flood lights.
-
Measures to add light if found necessary, should be implemented in the SSP for the different levels of security.
CCTV
-
Are all entrance points to the interior of the vessel monitored by the CCTV system?
-
Do you have a chart of the area covered by the CCTV?
-
Is there back up power for the CCTV?
-
List the location of CCTV monitors:
-
Do CCTV cameras cover any interior areas of the vessel, and if so where?
-
Are the crew trained in operation of the CCTV DVR to stop the unit from overwriting recordings?
Intrusion Alarm
-
What is the location of the intrusion alarm panel?
-
Does the intrusion alarm cover all doors and hatches leading to the interior of the vessel?
-
Are wing stations equipped with intruder alarm or can you lock the stations?
-
Is the swim platform equipped with an alarm?
COMUNICATIONS
-
Describe the types and locations of various communication systems on board.
FIREARMS
-
Describe the location of any firearms located on board.
OTHER CONCERNS
IF THE VESSEL HAS PREVIOUSLY HAD A SSP IN PLACE...
-
Verify security drills on drill matrix and have been carried out and logged.
-
Inspect the ships DOC - Declarations of Security<br>(Including the last ten ports have been filed correctly for PSC inspection)
-
Verify the AIS is properly programmed in accordance with SOLAS V/19
-
Onboard security training documented (verify by review of records)
Other
-
Verify the SSO (ships security officer) qualifications
-
Is access to files, programs and the alarm software on the yacht's computer system password protected?
-
Does the vessel carry valuable art?
-
Is the art equipped with contact alarms?
SUMMARY
REMARKS
-
The yacht is relatively small in relation to merchant ships and therefore represents less of a threat as a vehicle for terrorist acts.
The main risk is of unauthorized entry with the intention of acts against persons onboard.
The mitigation for this is access control in general and for restricted areas in particular.
The company access control policy is to man and/or automatically monitor access, or render inaccessible.
This reduces the overall manning demand and alleviates impact on operational effectiveness or crew fatigue. -
Additional Remarks
SUBMITTED BY
-
Enter name of IYC assessor.